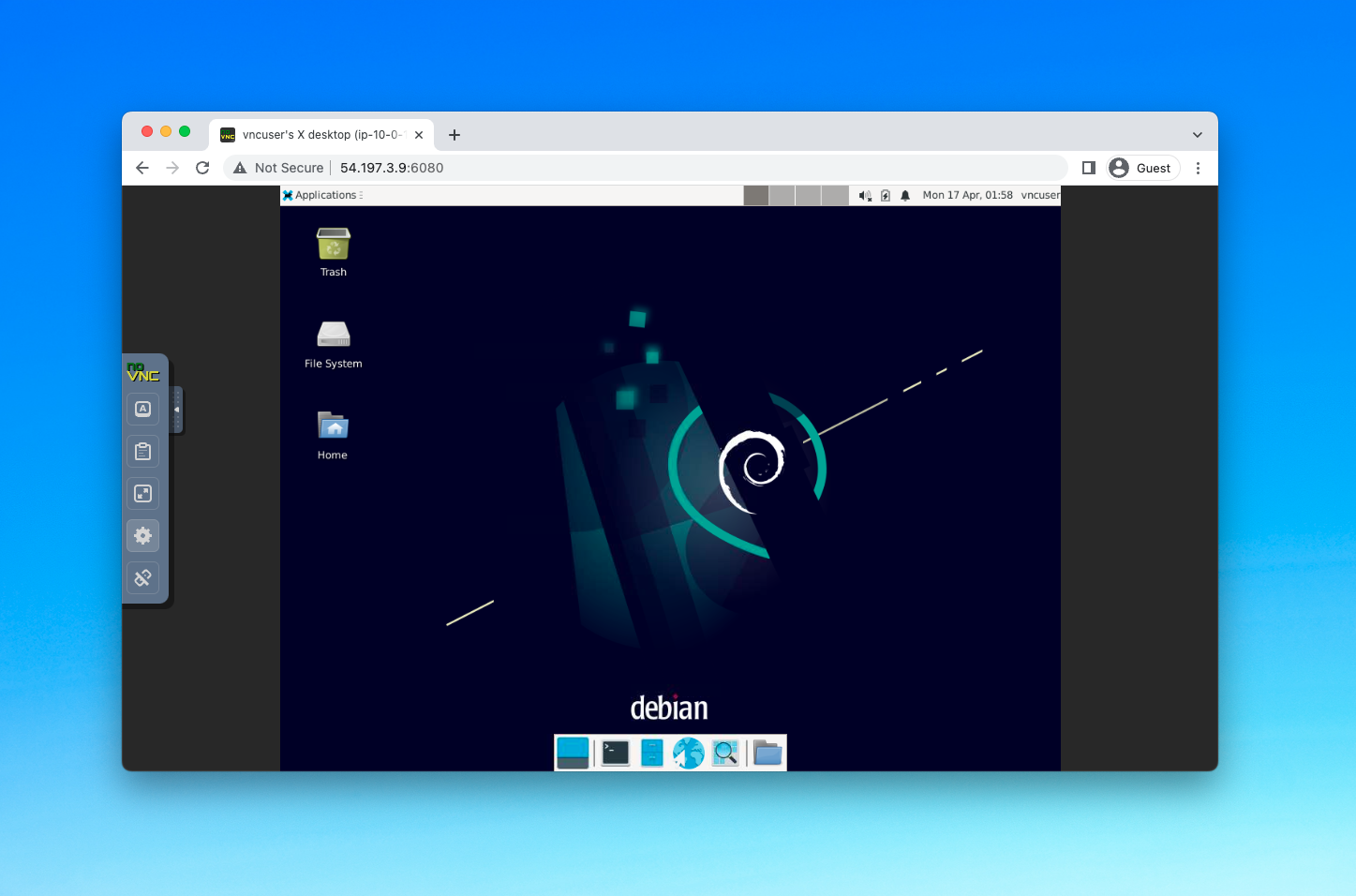
Control EC2 GUI Desktop from Web Browser
Use a VNC client online to access your EC2 instance
imageGUI desktop environments are helpful for many EC use cases. Unfortunately AWS doesnt provide an easy way to configure a desktop GUI. AWS offers managed services like Amazon WorkSpacesand NICE DCVexist but you lose the customizability and pricing offered by a raw EC.Since ECs ru...
How My Double Name Made Me a Better SWE
The importance of inclusive design in technology
imageIts not uncommon for me to come across software products that refer to my name as John instead of John Wright. Personally this has never bothered me a ton. Its not like John is wrong its technically my legal first name. But since I go by a double name and thats what all my family and friends call me seeing just John online doesnt feel right. To...
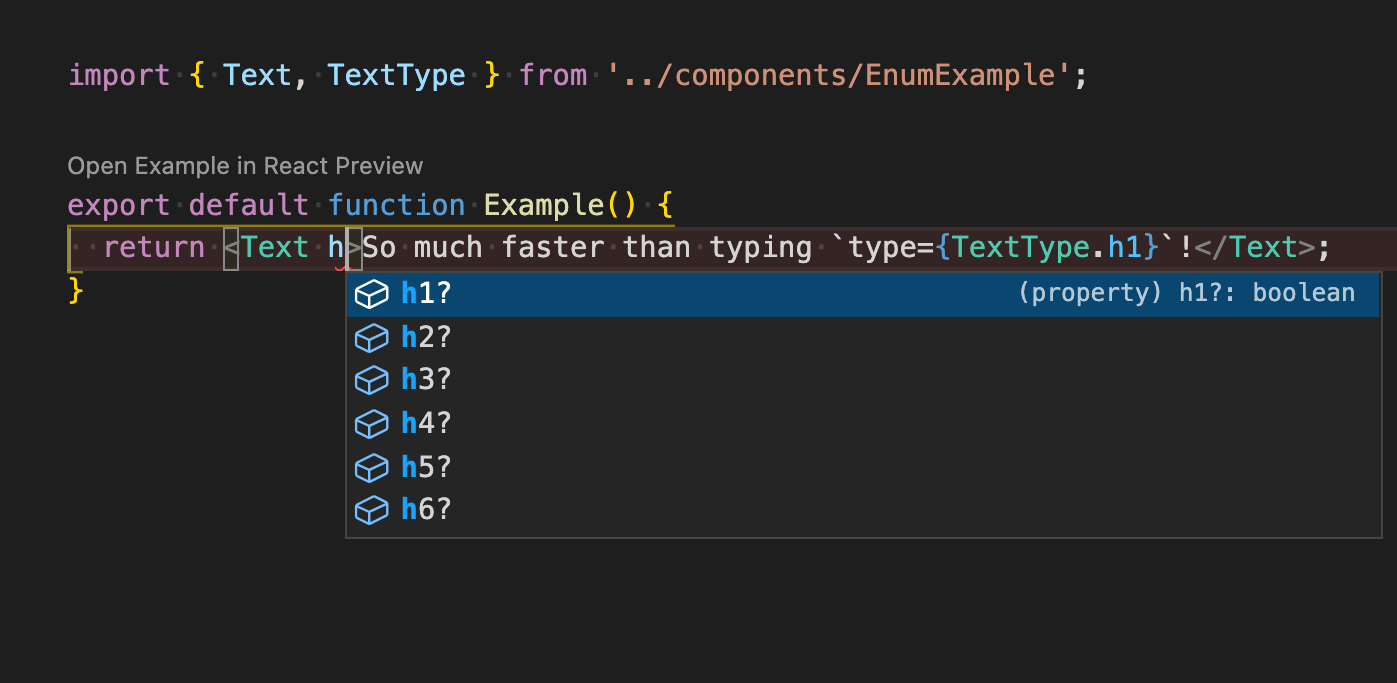
A Faster Approach to Enum Props in React
Create quick interfaces for your React components through powerful TypeScript definitions
Enums are one of the few features TypeScript adds to JavaScript beyond type checking. Combined with React enums are extremely useful in designing component interfaces.imageLets say were designing a text component in React. Well want different types of text so well add a prop to our component called type. Only certain typ...

Automating Lambda Schema Validation with TypeScript
Enforce and document your API's query and body params at runtime using TypeScript
API validation is essential to running a backend. Especially with tools like NoSQL databases it is up to the APIs business logic to enforce typing. Without these type checks security vulnerabilities can be introduced. Using TypeScript with Lambda is already awesome. Node.js is one of the fastest runtimes on AWS Lambda to cold start. Node.js also supports one of AWSs most mature SDKs.ima...

Handling Stale State from Scheduled Functions in React
Avoid creating stale closures with setTimeout() and setInterval() by using hooks to reference your logic
imageThe React Hooks API is widely becoming popular among the React community. Hooks enable components to supports features like state without needing to be written as a class.However hooks will sometimes act differently than expected. One common problem with useState hooks is the state not appearing to update in scheduled functions...

A Guide to Next.js and Serverless on AWS
Considering serverless for your Next.js website? Learn if its the best choice and how to implement
imageNext.js provides a ton of powerful features on top of React. With the ability to server side rendercontent Next.js gives you a fast website with great SEO.SSR also complicates your deployment strategy. With static websites like from Create React App or Next.js static...

Verifying SES Email Domain and DKIM Tokens in CloudFormation
Use custom resources to circumvent SES restrictions in CloudFormation and keep your IAC
imageTo send emails through SES AWS requires you to verify your email domain. Youre also required to create DKIM tokens to authenticate your emails. DKIM tokens help email clients detect malicious emails like spoofed addresses or phishing scams.If youre provisioning your next project with CloudFormation AWS currently doesnt offer any first party solut...

Port Forwarding WSL 2 to Your LAN
Run a public server from WSL thats accessible on your local network
imageThe Windows Subsystem for Linuxis great for development. WSL gives you the functionality of UNIX with only a fraction of the resources required for a traditional VM. It also runs alongside your Windows environment allowing you to access Windows files inside Linux. Microsoft continues to improve WSL like with the r...
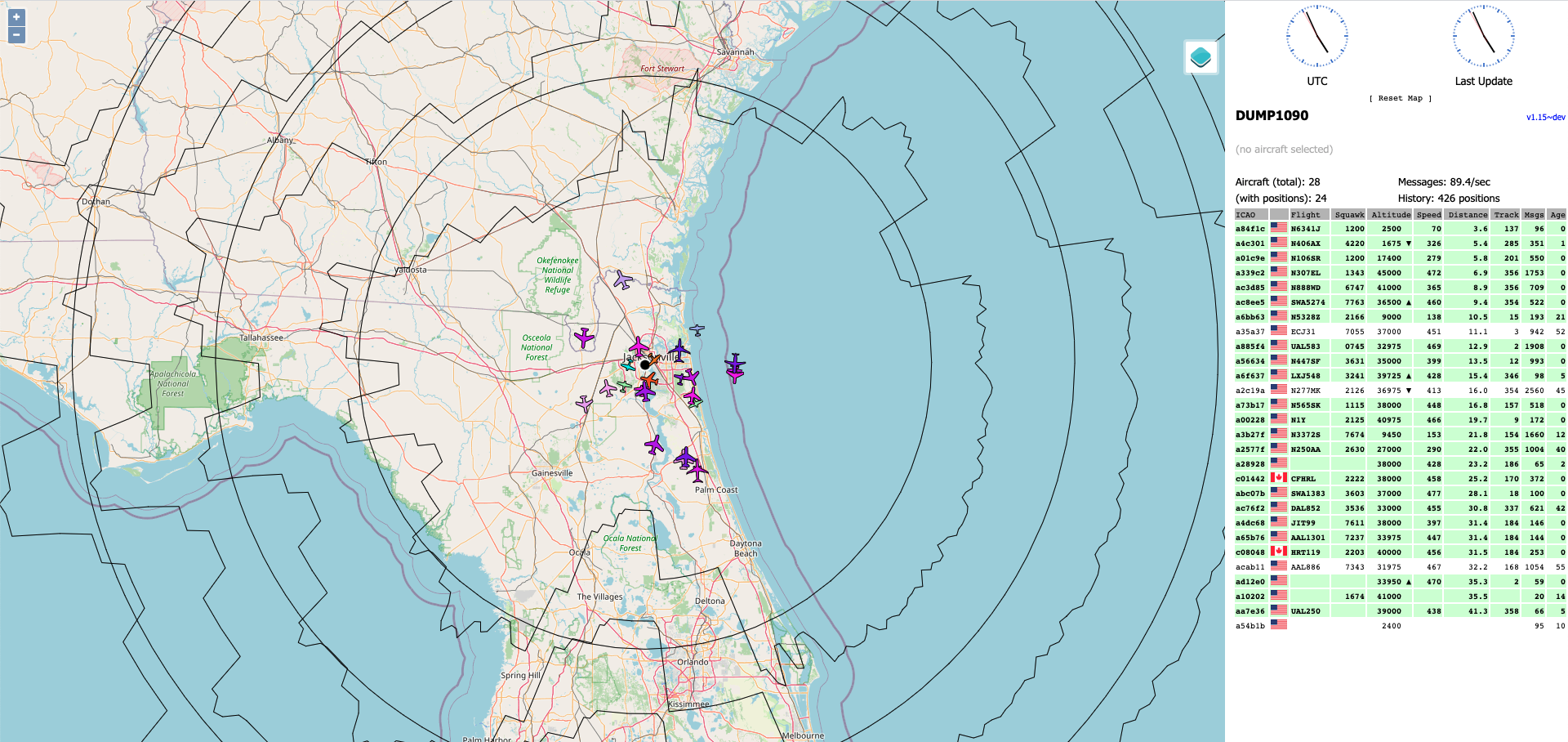
How to Track Airplanes with your own ADS-B Receiver
Use a Raspberry Pi to track local flights and get rewarded for doing so
Ever wondered how airplanes are tracked? Traditionally planes have been tracked with radar but limitations like weak oceanic coverage make radar not the best solution. However a new technology called Automatic Dependent Surveillance–Broadcast is emerging as the new standard for aviation tracking. What is ADS-B?Imagehttpsshop.jetvision.deWebRootStoreShopsMed...

How to solve SAM 403 Errors on CORS Preflight
The answer might be easier than you think: your OPTIONS method might be requiring authentication
If your browsers CORS preflight request is responding with a your APIs OPTIONS method could be requiring authentication. This might sound okay if your API is authenticated but the OPTIONS method behaves differently than other HTTP methods. Your API server will need to comply with the CORS standard which requires OPTIONS methods to work without authentication headers. How do CORS pref...